How to Remove a Hacker From my iPhone
How to Remove a Hacker From my iPhone- We use our iPhones for all: scheduling appointments, connecting with family and friends, banking online, and even keeping track of our health information. Because our iPhones store so much of our personal data, they’re a big target for unethical hackers.
How to determine whether or not your iPhone has been hacked, as well as some simple steps you can do right now to permanently remove the hacker.
What are some signs that my iPhone has been hacked?
Unfamiliar apps have been installed on your iPhone–
Swipe left on your Main screen until you reach the “App Library” display at the top. Scroll through your list of applications by tapping App Library. If you don’t recall downloading anything on this list, your cellphone may have been hacked.
Apple is selective about the applications it permits into the App Store. You’re more likely to end up with suspicious apps on your iPhone if you’ve hacked it or installed apps from somewhere other than the App Store.
If you share your iPhone with others, there are a few things you should keep in mind (or are using Family Sharing features), Apps you’re unfamiliar with could have been downloaded by someone you trust. Before you get too upset, see if anyone else in your family has downloaded the Unfamiliar apps.
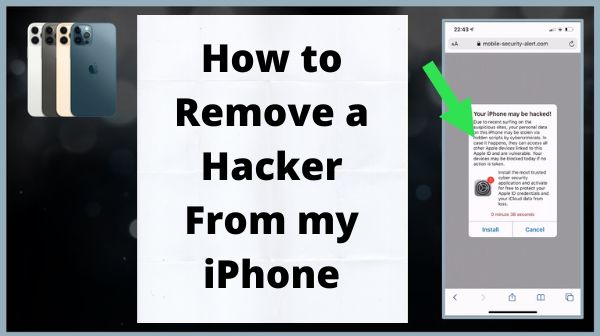
You’re getting frightening pop-up messages–
Pop-ups don’t always signal your phone has been hacked, but they can indicate that it has been infected with malware or spyware, specifically if you see them when you aren’t actively accessing the web.
If you encounter a pop-up saying “Your iPhone has been compromised!” or “We have identified that your browser is attacked with a trojan virus” when browsing the web, it doesn’t indicate you’ve been hacked. Most of the time, these pop-ups occur when you visit a malicious site (or has been hacked).
In reaction to these pop-up messages, never press on any link or make any kind of payment. You should not have to charge to have a virus eliminated from your iPhone.
There are configuration profiles in your settings that you are unfamiliar with–
A configuration profile is a set of options for managing email accounts, passwords, as well as other sensitive information. You may be required to install a configuration profile by your business or school in order to log into their accounts remotely. A hacker, on the other hand, could convince you to install a profile that grants them access to the phone.
Here’s how to find out–
To access Profiles & Device Management, go to Settings, General, and then click on Profiles & Device Management.
If you notice any profiles that you don’t recognise, you may have been tricked into installing them by a hacker.
Don’t be worried if you’re not seeing this part in your Settings. It simply signifies that no configuration profiles have been installed.
Messages are being sent to your contacts that you did not send–
If a hacker obtains access to your iPhone or Apple ID, they could be contacting your friends, family, and even others. Confirm your Messages inbox (and even your Email outbox) to be sure no one is claiming to be you as well as sending messages to others.
You can see the texts and calls they’ve sent whereas signing in with the same Apple ID you use on this iPhone if you sign into some other Apple device (such your family Mac or iPhone) with the same Apple ID you use here. Before you assume your iPhone has been hacked, ask your relatives if they made a call / sent the texts.
You’ve observed that your data use has increased–
Are you suddenly exceeding your data or calling restrictions despite the fact that you haven’t changed anything? Have you seen any unusual charges on your phone bill?
Your mobile data could be exploited by a hacker (or malicious software).
Tap Cellular / Mobile in the Settings app (based on your region).
To check which apps use a lot of data, scroll to the bottom to the “CELLULAR DATA” / “MOBILE DATA” area. Be cautious if you see something unfamiliar.
Your iPhone is slow or overheating–
You may have malware on your iPhone if it is extremely slow to open applications as well as access the internet. There might be malware running at the same time if your phone would seem to warm up a lot, specifically when you’re not using it or it’s not being charged.
When you’re playing the game and using other CPU-intensive applications, your iPhone can grow very warm—but it doesn’t always mean you’ve been hacked.
Battery is draining fast-
Go to Settings app and select Battery from the drop-down menu. What’s draining the most charge from your battery? If an application you don’t use very often (or have never heard of) is draining your battery, it could be the result of a hacker as well as malware.

How to Remove a Hacker From my iPhone?
Steps to Remove a Hacker From my iPhone
Off the Internet-
If you suspect someone has hacked your phone, off the internet will prevent the hacker from remotely accessing it.
If your cellphone doesn’t even have a Home button, slide down from top corner of the Main screen (if it does), or slide up from the bottom (if it does), and afterwards press the Airplane icon or mode to enter Airplane Mode. Click the Wi-Fi symbol (the curved lines) to remove if your phone remains connected to Wi-Fi while in airplane mode.
Remove any apps that you are unfamiliar with–
If you’ve loaded a harmful app on your iPhone by mistake, you can delete it to get rid of it. On your iPhone, removing unwanted applications is a lot simpler than it is on a PC, for example.
Simply tap as well as hold an app’s icon, then choose Delete App (or click on the X on the application if the symbol start jiggling).
Delete any configuration profiles that you are unfamiliar with-
If you find a configuration profile in Settings then click on General after that click on Profiles & Device Management that you don’t recognise, tap it and select Delete Account.
Clear the history in your browser–
If you’ve been getting scary pop-ups whereas surfing the web, delete your history, cache, as well as cookies to ensure they don’t appear again the next time you access your browser.
To clear history as well as web data in Safari, go to Settings, select Safari, then scroll to the bottom and click Clear History as well as Web Data. To confirm, click Clear History & Data.
Chrome: Open Chrome, click History, and afterwards Clear Browsing Data from three dots in the bottom-right corner. At the bottom, click Clear Browsing Data as well as choose All Time as the time range.
Your iPhone should be updated–
It’s possible that a security flaw in iOS allowed a hacker to obtain access to your iPhone. Because these security flaws are quickly patched, updating your iPhone should eliminate any backdoor entry points.
Make a new password–
Without your password, a hacker will have a difficult time accessing your iPhone. If you believe your iPhone has been hacked, your password may have been compromised, so reset it right away.
Use an older backup to restore your iPhone–
You can recover your iPhone to a point before this was hacked if you back that up to iCloud or a pc. If your iPhone has been hacked, this will uninstall whatever the hacker has downloaded to assist them keep control of your device.
You’re also reset your iPhone whenever you recover from a backup. This completely wipes your iPhone! You can recover from your backup following resetting if you’ve backed up or synced your data to iCloud or your pc.
Your iPhone should be reset-
You can execute a factory reset if you don’t have a record and yet still suspect a hacker is in control of your iPhone. This wipes your iPhone clean & reinstalls the os.
Anything you had synchronized to iCloud (even your texts) will be synced again to your iPhone once you log in along with your Apple ID. Anything nefarious that has been installed, as well as any backdoors installed by hackers, will be removed simply resetting your iPhone.
Read Also- 10 Best iPhone Hacks and Tips for 2022
How can I keep hackers out of my iPhone?
Activate the automatic update feature–
You’ll always be first to obtain the latest vital security upgrades if you enable regular updates for both iPhone as well as the applications you’ve installed.
Switch both switches to the On (green) state in Settings then General after that Software Update then click on Automatic Updates to enable automatic iOS updates.
Go to Settings then move to App Store and switch App Upgrades to the On (green) position to enable automatic software update.
Two step authentication should be used-
Two-step verification adds an additional step to the login procedure, forcing you to confirm all of your logins using an SMS text message or an authentication app.
Turn on two step verification for your Apple ID profile so you’ll always be informed if someone try logging in with your login details to any Apple service.
Click Settings, click your name at the top, click Password and Security, and afterwards click Turn on Two-Factor Authentication (if it isn’t currently on) to enable two-factor authentication.
Before you install an app, do some research on it–
Before installing the app, make sure to read the ratings or ratings in the App Store. You may also look at the “Data Used it to Track You” as well as “Data Linked to You” parts of an app’s App Store website to discover what kind of information it can gather about you.
If an application you’ve downloaded asks for access to your mic, camera, Bluetooth, photographs, or anything else you don’t want to share, say no when asked. The permission is required in some circumstances for the application to function, but you can grant it just when the application is being used to reduce risks.
Use a password that is both secure and unique–
Even if your password is larger than eight characters as well as comprises a combination of mixed-case letters, digits, and symbols, if you use it on different sites and apps, it won’t keep you safe. If a hacker obtains your passwords on a website as well as this is the same as your Apple Account, they could allow entry to your iPhone.
When utilizing public Wi-Fi, use a VPN–
Hackers may be capable to spy on what you’re to do if you join to an open Wi-Fi network, like at your school, a café, or the library. This indicates that going in to your internet accounts or entering your bank passwords when connected to public Wi-Fi could disclose your passwords without notice.
You may avoid this by utilizing a VPN whenever you access Wi-Fi outside of networks that you know are secure and reliable.






