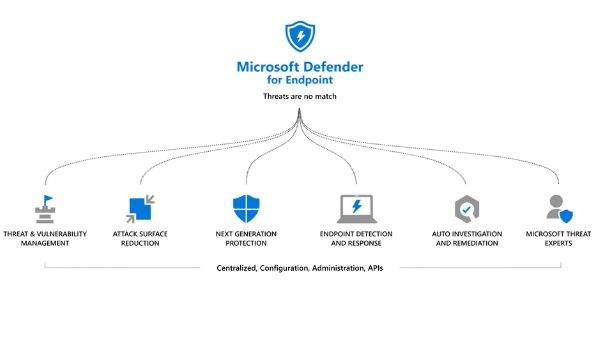
Microsoft Defender for Endpoint

What is Microsoft Defender for Endpoint?
Microsoft provides a high-quality endpoint security technology that can identify, research, and stop sophisticated attacks. By utilizing a number of technologies included in Microsoft Azure and Windows 10, it aids businesses in responding to attacks swiftly.
The following technologies are used by Microsoft Defender for Endpoint to safeguard business settings:
Endpoint behavioral sensors
direct behavioral cues from the Windows 10 os and process them. These sensors transmit this data to a separate, personal instance of Microsoft Defender for Endpoint in the cloud.
Analytics for cloud security
Microsoft uses big data analytics and device learning to translate behavioral signals into danger detections, insights, and suggested countermeasures.
Threat intelligence
Threat intelligence collected across the ecosystem as well as provided by partners is used by Microsoft’s threat hunters & security teams to deliver insights. Defender for Endpoint uses threat intelligence to identify attacker tactics, methods, and procedures (TTPs) and produce alerts.
Microsoft Defender for Endpoint Plan
It has two plan- Plan 1 And Plan 2
Functions offered by Microsoft Defender for Endpoint Plan 1
Next-generation protection
offers antivirus as well as anti-malware protection.
Manual response actions
enables security teams and professionals to take particular measures. When Defender discovers risks, for instance, they can send a file to quarantine.
Attack surface reduction
for hardening hardware and identifying zero-day attacks. Additionally, it offers fine-grained access control for your endpoints.
Centralized management and configuration
allows you to access the Microsoft 365 Defender site and the Microsoft Endpoint Manager integration.
Protection for other platforms
helps you protect devices running Windows, iOS, macOS, and Android.
Features of Microsoft Defender for Endpoint (Plan 2)
Defender for Endpoint was the previous name for Microsoft Defender for Endpoint (Plan 2).
Management of threats and vulnerabilities
Plan 2 offers the following threat vulnerability management capabilities:
- uses sensors to detect vulnerabilities and misconfigurations in real-time, eliminating the need for endpoint agents or recurring scans.
- Prioritizes vulnerabilities in accordance with the threat environment, sensitive information on exposed devices, internal organisation detections, and enterprise context.
- Offers real-time protection.
- Completely cloud-based platform
- Integrates with the app analytics skill set and the Microsoft Intelligent Security Graph.
Attack Surface Reduction
Attack surfaces are areas of your business where attacks and online threats could succeed. Defender for Endpoint may lessen endpoint attack surfaces. In addition to these features, web and network protection controls access to harmful domains, URLs, and IP addresses.
Next-Generation Protection
Anti-malware features that go beyond those of traditional antivirus, which relied on signature-based threat identification, are referred to as next-generation security. Here are some of Plan 2’s main characteristics for next-generation protection:
Heuristic antiviral protection that is behavior-based, real-time, and includes continuous scanning based on the observation of file and process behavior
detects and prevents “unsafe apps,” which, despite not strictly being considered malware, can still harm a system.
offers cloud-delivered protection, which includes identifying and thwarting new and unidentified threats.
Endpoint Detection and Response
Full EDR functionalities are available in Plan 2 to provide quick detection and action. This makes it possible for security analysts to priorities warnings, gain insight into the full extent of a breach, and deal with threats right at the endpoint.
This system continuously gathers behavioral cyber telemetry with the assumption of a breach. This data consists of user login activities, deep optics into the memory manager and kernel, deep optics into the network activity, process information, deep optics into the memory activity, and more.
The EDR workflow is as follows:
The system generates alerts when a threat is found, causing the analyst to look into it.
The system creates an incident object out of all the warnings linked to the same attacker or set of attack methods.
Analysts can work together to collectively examine and mitigate threats across several endpoints once the system has aggregated notifications in this fashion.
Threat detection and data exploration
The system keeps track of security incidents for six months, allowing an analyst to go back to the moment the attack took place. The analysts can then change their perspective by applying new filters. This enables direct intervention on the attacked endpoints to evaluate and eliminate threats.
Automated Analysis and Correction (AIR)
Key skills of Plan 2 automated inquiry and remediation include the following:
checks for breaches, notifies them, and takes prompt corrective action.
reduces the number of notifications, allowing security operations to focus on higher-value jobs and more complicated threats.
offers an action center with the option to approve, reject, or undo completed activities that tracks all remedial actions, both pending and completed.
Microsoft Secure Score for Devices
The dynamic analysis of an enterprise network’s security condition is a component of Plan 2 as well. It finds vulnerable systems and takes the necessary steps to improve an organization’s security.
The threat as well as vulnerability management dashboard of the Microsoft 365 Defender portal displays this score. An improved score shows that endpoints are better protected against cybersecurity threat threats.
The following categories are used to display the general security setup status of networked devices:
- Applications
- Operating system
- Network
- Accounts
- Security controls
Experts in Microsoft Threats
Security Operation Centers (SOCs) can receive expert-level analysis and monitoring from Microsoft Threat Expert. This managed threat detection solution aids your SOCs in making sure that businesses don’t ignore serious risks in their surroundings.
The Threat Professionals solution gives internal security experts access to specialists as needed and specialist-driven insights as well as data through targeted attack warnings.
Pros and Cons of Microsoft Defender for Endpoints
Here are some of Microsoft Defender for Endpoint’s Pros and cons–
| Pros of Microsoft Defender of Endpoint | Cons of Microsoft Defender of Endpoint |
| All Windows endpoints come with the basic edition for free. | Only Windows supports web blocking. |
| interoperability with a wide range of endpoints, including Windows 10, Windows Server, Linux, macOS, iOS, and Android. | The endpoint agent on Linux has a comparatively large memory footprint. |
| Multiple Microsoft products, such as Exchange Online, Sharepoint, Microsoft Teams, OneDrive, Azure Active Directory (AD), and Azure Identities, are covered by a single subscription. | Anti-virus software is not very customizable. |
| Detects indicators of compromise (IoC) based on MITRE definitions when mapped against the MITRE ATT&CK knowledge base. | Outside of Windows environments, some customers experience deployment issues. When deploying MDE, there are several procedures involved, especially for older macOS computers. |
| use information obtained by the Office 365 applications’ billions of signals. | ———- |
| creates a graphic attack timeline using all the data associated with the same attack. | ———- |
| using the KQL query language for sophisticated threat hunting | ———- |
| Retention of log data for 180 days | ——— |
Endpoint Security- Cynet 360’s prevention, detection, and protection capabilities
A full Endpoint Protection Platform (EPP), Next-Generation Antivirus (NGAV), as well as automated incident response are all included in the security program Cynet 360. By providing a “all in one” security approach, Cynet makes it simpler to implement a modern security toolset: Cynet 360 offers network analytics, UEBA, and deception technology in addition to endpoint protection.
- Microsoft Releases Windows 11 Build 22000.434 – Here’s What’s New
- Microsoft and iFixit Team Up on Official Repair Kits for Surface Devices
- Microsoft And Samsung Could Team Up On New AR Headset And Introducing HoloLens 2
The Cynet platform consists of:
NGAV
Blocked malicious payloads include malware, exploits, LOLBins, Macros, malicious scripts, and other predictable and unpredictable threats.
Zero-day protection
Blocks unexpected threats and detects suspicious behavior using User and Entity Behavior Analytics (UEBA).
Monitoring and control
Assessments of endpoint vulnerabilities, application control, asset management, and auditing, logging, and monitoring.
Response orchestration
For repairing compromised endpoints, networks, and user accounts, automated playbooks and remote manual intervention are used.
Deception technology
Attracts attackers to a seemingly weak honeypot, reducing damage and gaining vital information about attack strategies.
Network analytics
Detecting lateral movement, shady connections, and odd logins.
People May Ask
What does Microsoft Defender for Endpoint do?
For Windows, macOS, Linux, Android, iOS, and network devices, Microsoft Defender for Endpoint provides market-leading endpoint protection and aids in the quick stoppage of assaults, scaling of security resources, and evolution of defences.
What is Microsoft Defender for Endpoint license?
The prevention/EPP focus of Microsoft Defender for Endpoint P1 includes: Next-generation cloud-based antimalware with built-in AI that aids in stopping ransomware, known and undiscovered malware, and other threats in their tracks.
Is Microsoft Defender endpoint protection?
Enterprise endpoint security platform Microsoft Defender for Endpoint is made to assist enterprise networks in preventing, detecting, looking into, and responding to sophisticated threats.